In today’s digitally driven world, cyber threats develop at a unique speed. From ransomware attacks to sophisticated fishing plans, organizations must face continuous risks that can compromise sensitive data, disrupt operations and damage reputation. This increasing complexity has made cybertrusselin (CTI) an essential component of modern cybersecurity strategies.
What is Cybertrussel Information?
Intelligence of cyber rights refers to collecting, analyzing and interpreting information about existing or new cyber threats. The goal is to provide action-rich insights that help organizations prevent frequent attacks, react effectively to events and strengthen their overall security posture.
CTI is out of traditional security measures. Instead of responding to fractures after their occurrence, companies can estimate dangers, understand the attack, and apply preventive defense.
Active Hazard Prevention
CTI helps organizations discover potential dangers before they grow to full-scale attacks. By analyzing the pattern, the indicators of the compromise (IOC) and hacker techniques, safety teams can estimate risks and continuously use rescue.
Increased Reaction to the Event
When an online attack occurs, timely and informed action is essential. The father incorporates the event response teams regarding the species, potential targets, and potential impact of the intelligence attack. This allows rapid control and mitigation, reducing damage.
Better Risk Management
Understanding the scenario with cyber danger allows companies to assess weaknesses and effectively prioritize resources. CTI reports decision-making processes that assets require the most protection and that pose the most significant risk.
Security Against Advanced Hazards
Modern cyber attacks often use sophisticated strategies, such as zero-day exploitation, harmful software, and social engineering.. The threat of threats helps organizations to recognize these advanced dangers quickly and distribute appropriate countermeasures.
Support for compliance and governance
Regulatory structures such as GDPR, HIPAA, and PCI DSS require organizations to maintain strong cybersecurity measures. CTI helps meet these standards of consistency by providing evidence-based assessments and mitigation strategies.
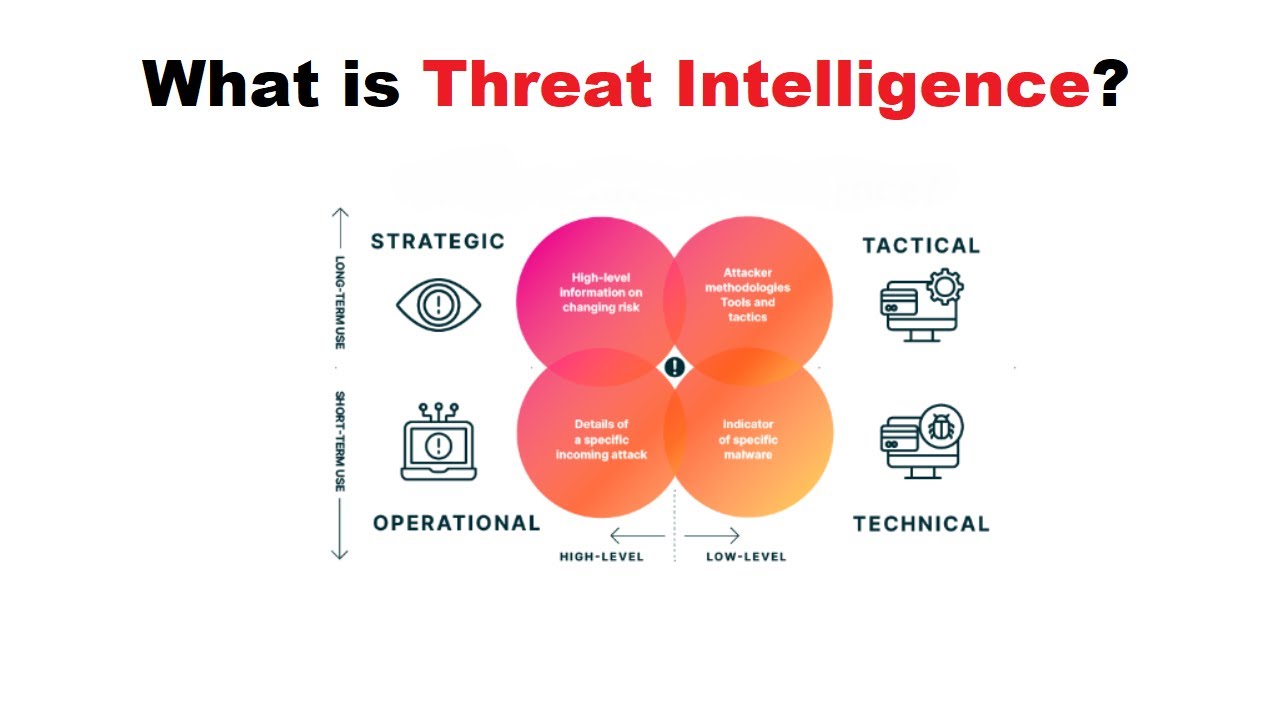
Essential Components of Cyber Danger Intelligence
- Strategic intelligence: Attacker focuses on understanding techniques and equipment. This helps the security teams identify immediate dangers and strengthen the defense mechanism.
- Operational intelligence: The attacker provides insight into attacks or campaigns, including goals, methods, and possible goals.
- Strategic intelligence: Provides extensive perspectives on cybersecurity that affect trends, new dangers, and geopolitical factors. This level indicates a long-term security plan and investment decisions.
Strategies to Apply Effective Cybertrusselineligens
- Collect and integrate data: Collect data from many sources, such as threat feeds, security logs, and Open-SOS Intelligence (OSINT). Integration of this information ensures a comprehensive approach to the hazard landscape.
- Give and prioritize hazards: Not all threats are equally important. Use analysis tools to classify risks based on severity, probability, and potential organizational impact. This priority enables efficient resource allocation.
- Explore Network benefits from AI and machine learning to monitor activity, detect deviation, and generate notifications. The automation response accelerates the time and reduces the load on the security teams.
- Collaborate and share intelligence information. Information sharing participates in local communities, industrial forums, and partnerships. Collaboration improves the visibility of danger and provides access to the latest intelligence from other organizations facing similar challenges.
- Updated and delimited continuously, Cyber threats are constantly evolving. Regular hazard company processes and equipment updates ensure organizations are prepared against new risks.
Conclusion
Cyber Threat Intelligence has become the cornerstone of modern cybersecurity. When cybrants grow in sophistication, organizations cannot rely on fully reactive measures. CTI allows businesses to estimate threats, respond effectively, and make informed security decisions.
By investing in strong defenses, companies not only protect their digital assets, but also strengthen customers’ trust, protect their reputation, and ensure long-term flexibility in a rapidly hostile cyber environment.



